Organization’s has different set of challenges in managing the risk related identities and access. As a CIO its important to understand where we stand with respect to managing access reviews with in the organizations. An attempt can be made to understand the existing situation with respect to the access review and compliance to assess “as-is” vs “to-be” state gaps.
Performing Self-Assessment:
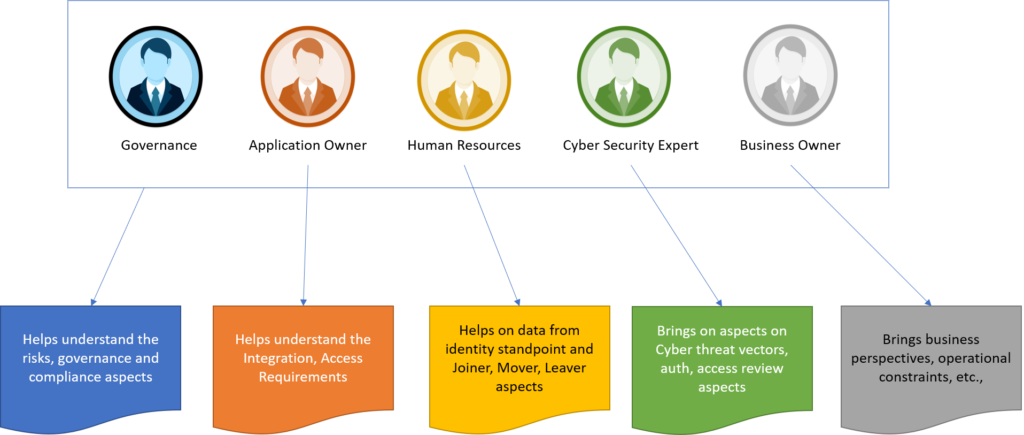
As an organization there are various stakeholders who needs to be involved in the Self assessment exercise to understand the “AS-IS” situation. Assessment can be made and documented using different tools including SWOT, Fishbone Diagrams, Nadler-Tushman’s Congruence Model, McKinskey 7s Model to understand the components to identify the gaps. The different stakeholders to get involved any why they are needed are outlined here.
Self Assessment Questions
The following questions could also be very helpful for introspection on how much we are following Access control and review practices in the organizations.
Auditing/Compliance
- Is access permissions provided and revoked are logged and auditable?
- How long the audit logs of access reviews are available?
- Whether any change in reporting manager is logged and appropriate access reviews are auto assigned?
- Can audit logs be shared when by requested ethics committee/legal team disputes ?
- At what frequency the access reviews are happening ?
- What happens on denied access related disputes ?
- In what ways access permissions to obsolete or legacy applications managed?
- How the currently reported audit recommendations are managed with respect to Audit governance?
- How is the Separation of Duties(SoD) enforced as part of the compliance with respect to Audit compliance ?
- Does all the applications provide entitlement visibility for better controls ?
- Does the compliance requirements in the organization have access review certifications needs.
Access Review and HR Processes
- Are we sure the employees have the right level of access to the applications or IT Assets?
- If employee is promoted what level of privilege’s are provided (excessive or limited permissions)
- Has any applications has been updated and has newer entitlements or permissions added?
- Does permissions are being appropriately revoked and added while transfer happens between departments ?
- Whether the access level changes are enforced when an employee is added or removed from group?
- What happens to access when employees go on long leave ?
- What is the access review mechanism on terminated employees ?
- Do we have birthright provisions that employees are entitled to?
- Is the access control to applications are to be controlled by geography?
- Are there multiple levels of workflows for access approvals?
- Is governance group involved in the approval process ?
- Whether the access rights are grouped by role?
- Does role elevations are part of promotion or department transfer?
- Is there sensitive entitlements which requires higher level of reviews and monitoring ?
- Is appropriate attributes are being managed at the time onboarding ?
- Based on evolving business requirements when attributes are added how its impacting the Access review processes?
- What happens when employees need to access applications after exit? Is there such needs?
- Is SOD evaluation done before access being granted ?
Provisioning
- Are the access approvals are auto approved ?
- What is the access review mechanism for access which are auto approved?
- Whether applications enable provisioning automatically upon schedule?
- How the change control process happens in provisioning ?
- Does the target applications provide API or SDK for managing permissions?
- How the access approval on manual provisioning validated ?
At iRarity we can help discover the answers for this kind of questions. Also help in assessment which can help in selecting the right tools for Identity Access Management. Do share your comments on any other questions which might help in performing better self assessment.
