When a new employee gets hired in your organization, you have to provide specific access to them corresponding to their position within your company. It will be manageable when we have to provide a limited number of access to the end application. But when the number of access exceeds, it will be hard to manually assign much access to a single employee.
So here Sailpoint introduces the concept of “Roles” also known as “Bundles”.Roles contain multiple entitlements within themselves. It Follows the “One too many” mapping.
One or More entitlements can be dumped into a single Role. In simple words, a Role is an object that encapsulates a set of access.
Let us Consider an Example,
An employee named John has joined your organization as a Developer and he needs to provide with (Read, Write and Modify) access in the “Developer Application”. Here we can create a role named “Developer Role” and map those (Read, Write and Modify) entitlements into it. When the Role is assigned to that employee, he will automatically get those access that is mapped with that role.
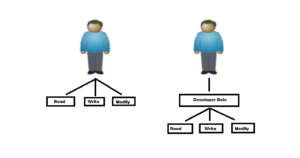 So whenever a new employee has been hired as a Developer, we can directly assign the “Developer Role” to them rather than assigning entitlements manually.
So whenever a new employee has been hired as a Developer, we can directly assign the “Developer Role” to them rather than assigning entitlements manually.
Common Role Models:
Single Tier, Two Tier, and Multi-Tier Role Modelling Architecture are the most common role models which most Enterprise follows.
Two Tier Role Modelling Architecture is Recommended by the Sailpoint.
Types of Roles:
1.) Organization Role – Organization Role in Sailpoint is nothing but a Folder Role. The only use case behind this Role is to create the structure.
2.) Business Role – It is a common role we see in today’s world like Manager, Application Analyst, Developer. These are the different kinds of roles in which a person
can join your organization
3.) IT Role – If anybody is joining as a Manager(Business Role) in your organization, IT Role provides the list of applications that he can access.
- Business Roles and IT Roles will be interlinked using “Controlled Association”.
- Controlled Association is “Required” and “Permitted” relationship.
- Required – whichever IT Role is mapped in “Required” fashion, will be assigned as a birthright role.
- Permitted – whichever IT Role is mapped in “Permitted” fashion, the user will be permitted to request for that role.
- This Controlled Association helps us to avoid the problem of Role Explosion and Role Duplication.
4.) Entitlements or Permissions – Inside each IT Role, it will further define what entitlement or permission the users will have.
Example – The User can have the (Read, Write and Modify) permissions in the “Developer Application”
