Introduction
In the digital world, data is the most important thing. Everyone is trying to protect their sensitive information from everywhere. If we take an enterprise they have more responsibilities to protect their data in terms of compliance and other regulations. Nowadays, All Enterprises are implementing an Identity Governance solution for protecting user information and allowing access to applications, yet they failed to control the Data. What is the solution to this problem ?
The Sailpoint leading Identity and Access Management Software provider has come up with a product called File Access Manager(FAM). FAM is one of the leading Data Access Governance tools which provides the solution for unstructured data governance. It helps to identify and classify where sensitive data resides on your network and cloud-connected storage applications, establishes data ownership, mitigates security risks with monitoring and forensic analysis of file storage systems, and assists in meeting compliance and audit requirements by enforcing policies related to data access. File Access Manager(FAM) formerly known as SecurityIQ(SIQ).
Before getting into FAM, We can see more about Structured data vs Unstructured Data examples.
1.Structured Data vs Unstructured Data
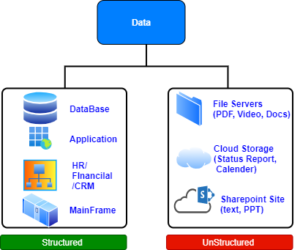 i) Structured Data:
i) Structured Data:
- Structured data simply means any form of data that easily fits into a relational model or a set of database tables.
- It can be protected by their own system so no need to provide secure access separately.
- These items can be managed easily through Identity and Access management tools
ii) Unstructured Data:
- Unstructured data simply means any form of data that does not easily fit into a relational model or a set of database tables.
- It can be a PDF, Word Document, Text, Email, Image, Video, or Audio file
- It may be stored in Network File Share, Cloud Storages (Dropbox, Box, GDrive, etc), and Sharepoint sites
- These Data cannot be managed through Identity management tools
2.How FAM secure Unstructured Data?
- FAM is specially made to handle unstructured data
- It can help to get a complete view of where the sensitive data lives and what sensitive information it contains.
- FAM retrieves application resources with their permissions (Read, Write, and Full control).
- Resources will be classified into different categories, based on the sensitive file types.
- It can help to report compliance aspects based on PII, PCI, and PHI from compliance (GDPR, HIPPA, SOX, etc)
- Provide Access Review, Data owners can analyze the permission and approve the appropriate user’s permission.
- Real-time activity monitoring, Data owners get all the Event notifications and policy violation alerts based on this they can make a decision immediately.
3.FAM Featured / Benefits
- Data Discovery and Classification- Discover sensitive data from files based on keywords, wildcards, regular expressions and metadata, and how files are accessed by users.
- Permission Analysis – Evaluate user access to data and how it was granted. Analysis shows access models and ineffective/overexposed permissions.
- Content and Behavioral Analysis – Classify folders based on the groups or departments accessing the data. Which helps to identify the sensitive files. Provide advanced data classification using OCR (Optical Character Recognition) to scan the image file stored in PDF or DOC.
- Crowdsourced Data Owner Election – Innovative crowdsourcing technology accurately identifies and elects proper data owners by enlisting input from users of the data.
- Compliance Policies – Pre-defined policies are designed to accelerate readiness with PII, PHI, and PCI-related compliance requirements such as GDPR and HIPAA also customize more policies using rules.
- Data Access Certification-Effectively and accurately respond to audits with automated access reviews and certifications.
- Real-time Activity Monitoring-Track user activity for greater security insight. Monitor access policy violations in real-time with automated alerts and responses.
- Flexible Deployment Options-Can Deploy on cloud platforms, including Amazon Web Services and Microsoft Azure, or in the data center on-premises.
- Complete Support for On-premises and Cloud Data:
- File Servers and NAS: Microsoft Windows, Hitachi, EMC, NetApp
- Portals: Microsoft SharePoint and Microsoft SharePoint Online
- Mail: Microsoft Exchange and Exchange Online
- Cloud storage: Microsoft OneDrive, Box, DropBox, Google Drive
- Corporate directory: Microsoft AD, Microsoft Azure AD
Keep visiting our blog to see more posts about File Access Manager and Implementations.
